Modern DLP options should present real-time instructional prompts to users when non-compliant behavior is observed. Tanium provides the main Converged Endpoint Management (XEM) platform that empowers you to manage and safe your endpoints from a single console. With Tanium, you probably can data loss prevention achieve real-time visibility into your information and gadgets, no matter where they’re located or how they’re related. You can also use Tanium to implement granular policies and controls to stop knowledge loss, comply with laws, and automate endpoint actions to remediate points and incidents in minutes, not days. As organizations traverse the expansive cloud landscape, extending knowledge loss prevention measures to the cloud turns into imperative.
- To successfully assist the program, undertake safety insurance policies which are consistent with DLP aims.
- The management over knowledge that DLP options present can empower organizations to choose out the extent of confidentiality for every record and configure how the system reacts to signs of knowledge safety incidents.
- It also outlines how information can be used by authorized people without by accident exposing it to other entities.
Community Safety Controls: Vigilant Monitoring Of Knowledge Motion

Protecting information is becoming ever tougher as a end result of an organization’s knowledge could be used or saved in a quantity of codecs, in a number of locations, by various stakeholders across organizations. Moreover, completely different sets of knowledge might must comply with different guidelines based on sensitivity ranges or relevant knowledge privateness regulations. Syteca is very flexible and customizable, allowing for adjustments to fulfill your organization’s specific wants. In addition, Syteca can help you meet the requirements of many cybersecurity standards, legal guidelines, and rules. A data leak, or data leakage, is an unauthorized but unintentional transmission of sensitive data from an organization’s perimeter. Leaked delicate information could additionally be uncovered publicly or used maliciously by third events to perform a cybercrime similar to identification theft.
Discover Shadow It, Optimize Spends And Govern User Entry In One Platform
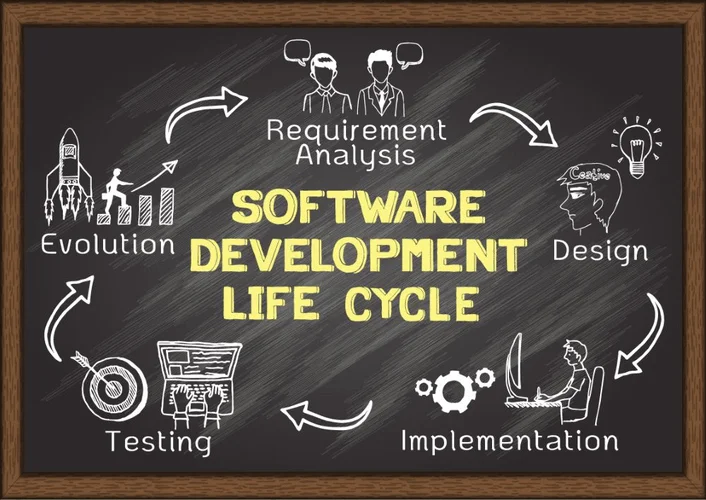
The organization also needs to ensure that the DLP solution is fully built-in throughout the company’s cybersecurity structure. Data loss prevention (DLP) is a set of tools and processes used to ensure that sensitive data just isn’t misplaced, misused, or accessed by unauthorized users. Major data loss prevention corporations are working to increase their geographic boundaries globally by introducing industry-specific options. These firms strategically interact native partners to achieve sturdy regional affect. In addition, main corporations out there are launching new products to draw and keep their clients. Therefore, by adopting such strategies, gamers will maintain their competitiveness in the market.
Do You Might Have Remote Employees Or Byod Policies?
Another best practice for knowledge loss prevention is prioritizing knowledge classification, which helps organizations establish and safeguard their most delicate information. DLP finest practices make positive that delicate knowledge is correctly recognized, categorized, and guarded. Additionally, educating stakeholders and conducting regular safety testing enhance total knowledge safety whereas reducing the likelihood of breaches. Content-aware DLP tools analyze information content material, including text, pictures, and recordsdata, to identify sensitive information corresponding to personally identifiable information (PII), monetary data, or intellectual property. These instruments employ advanced algorithms and machine studying methods to classify and defend delicate information accurately.
You can tackle potential safety threats earlier than they escalate into major incidents. By carefully following business tendencies and updates on information safety threats, you can adapt your DLP strategy as needed. Measure the effectiveness of your DLP strategy using key efficiency indicators (KPIs), which can observe elements like the variety of blocked knowledge transfers and detected policy violations. You can establish a suggestions loop with end-users to identify areas for enchancment and cut back false positives that disrupt user workflows. A well-crafted Data Loss Prevention (DLP) technique acts as a defend, defending your group from costly knowledge breaches and reputational damage and ensuring you meet regulatory necessities. Analytics can pinpoint the functions that make the greatest use of high-risk knowledge and should influence how cybersecurity is carried out throughout an organization.
Maintain open communication traces through a collaborative platform for continual customer enter and queries, supporting steady iteration as enterprise demands change. File Security Solutions, corresponding to Imperva File Firewall, are an important a half of a DLP strategy. Such options safeguard knowledge at rest and knowledge in use, and detect leaks of file-based information. It identifies and prevents the misuse or unauthorized sharing of sensitive information. This is because the unintentional leakage or lack of sensitive data due to a malicious actor, an inside job, or an unknowing worker, can lead to significant financial loss and reputational injury to any group. Strengthen your organization’s IT safety defenses by keeping abreast of the most recent cybersecurity information, options, and best practices.
When researching a DLP vendor, be sure that they will demonstrate any state of affairs involving the safety of your Intellectual Property. The best strategy that fits this scenario is to offer an exception for the Sales group members. DLP for Endpoint can also detect HTTP/HTTPS, which could be done with superior utility configuration. This is the time to kick the tires and guarantee the product meets your compliance needs and observe deficiencies in your triage process. Consult with friends in your trade and find out who they’re utilizing for DLP and gauge their satisfaction with support, incident workflow, and total confidence level.
Evaluate options like data classification, content material inspection, and user activity monitoring to choose the most effective solution for your company. Consider each on-premise vs. cloud-based DLP options, as together, you have greater management with options which may be typically easier to deploy and keep. Ensure the chosen DLP resolution integrates seamlessly with your existing safety infrastructure, as compatibility issues can lead to operational inefficiencies. Monitor your methods for unusual exercise that may indicate a possible data breach. This consists of monitoring data transfers, unauthorized access attempts, and suspicious entry patterns in your community visitors. This allows enterprises to protect their belongings, adjust to laws, and scale back risks to their status and operations.
Digital Guardian’s cloud-delivered DLP Platform detects threats and stops information exfiltration from each well-meaning and malicious insiders as properly as exterior adversaries. The escalated adoption of the cloud for knowledge storage by main corporations is a key factor driving market progress. The South America and the Middle East & Africa markets are influenced by increased technology adoption, rising smartphone penetration, funding information safety, and a large-scale acceptance of cloud know-how. The finish level phase is predicted to develop at the highest CAGR in the course of the forecast period. Increased reliance on remote work, rising cyber security threats, and regulatory necessities are driving product adoption. In addition, technological developments and the necessity to safeguard delicate data contribute to the continued growth of the tip point DLP phase.
In an period the place data breaches and cyber threats are more and more common, defending delicate information is a top precedence for organizations. Data Loss Prevention (DLP) is a crucial aspect of any complete cybersecurity strategy. It entails a set of instruments and processes designed to make certain that sensitive information just isn’t lost, misused, or accessed by unauthorized customers. This article delves into the essentials of DLP, providing concrete recommendation and examples to help your group successfully safeguard its information. DLP tools and software play a vital role in upholding data safety insurance policies and preventing data loss. Popular DLP tools embrace Digital Guardian DLP, Forcepoint DLP and Symantec Data Loss Prevention.
Real-time information loss prevention systems continuously monitor information flows, permitting firms to catch and react to any suspicious activity or potential data breaches. In addition, the pandemic accelerated the adoption of cloud-based services and purposes. While cloud applied sciences provide many benefits, in addition they pose new challenges in knowledge safety and privateness. As companies adapted to new working models, the DLP market noticed an uptick in demand for solutions throughout COVID-19, addressing endpoint safety, cloud data protection, and insider threat detection.
Mass remote working has also added an entire new fleet of doubtless unmanaged endpoints to the combo. Effective DLP goes beyond technology; it integrates seamlessly with present business processes. Organizations ought to assess and align DLP methods with day-to-day operations, making certain minimal disruption while maximizing knowledge protection. This strategic integration ensures that DLP becomes an enabler somewhat than an impediment to enterprise functions. Because one provider may not cowl all DLP parts, select distributors who can safe knowledge throughout several recognized use instances, or combine it with other instruments. Before selecting a solution, thoroughly test it to verify that it meets the needs of the business and is effective.
A DLP program is just as good as the individuals implementing it and people are your employees, in every division. So, frequently train employees on the importance of DLP, how to recognize potential threats, and best practices for data security. It’s vital to make use of real-world examples to spotlight potential dangers and consequences of knowledge breaches so that they grasp the far-reaching authorized penalties. A step-by-step guide is crucial for constructing a sturdy Data Loss Prevention (DLP) strategy, which will give your organization a aggressive benefit. It ensures a methodical strategy to facing the myriad security threats with confidence.
Develop a complete framework that captures data on consumer exercise, potential security incidents, and DLP coverage violations. IT teams can leverage detailed logs to analyze suspicious exercise, whereas compliance officers can generate reports demonstrating adherence to specific rules. For executive management, high-level dashboards can present a clear overview of total information security posture. The Reveal Platform by Next is a comprehensive information loss prevention solution that is simple to make use of and supplies organizations with instant advantages. Reveal educates employees, discovers risks, and enforces data handling insurance policies to forestall information loss. To embark on a journey of effective knowledge loss prevention, it’s crucial to grasp what a knowledge loss prevention strategy actually encompasses.
Additionally, organizations should assess third-party distributors for compliance with safety standards and set up a robust incident response plan to address potential threats swiftly. A Data Loss Prevention Assessment is a complete evaluation of an organization’s DLP policies, instruments, and practices. It involves analyzing the organization’s knowledge flows, figuring out vulnerabilities, and assessing the effectiveness of present DLP options in defending delicate information. The evaluation provides insights into areas that require enchancment and helps organizations develop a strong DLP strategy tailored to their specific needs. It also considers the functionality of DLP solutions in coping with particular threats like false positives, which can burden security teams with unnecessary alerts. Moreover, as information privateness regulations turn into stricter and the potential financial penalties for data breaches increase, the importance of a thorough DLP danger assessment cannot be overstated.
Transform Your Business With AI Software Development Solutions https://www.globalcloudteam.com/ — be successful, be the first!